Hi,
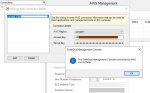
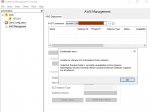
I am trying to configure Scaleout on AWS. I created an AWS connection providing access/secret key. But I got below error when I got to AWS deployment tab. Can you find out why this keeps happening.
Further I want to know is there a way to connect to AWS without providing access/secret keys may be such as using IAM user, roles etc. I am reluctant to use access/secret keys as we have to rotate keys periodically, and lack of security.
Appreciate your inputs on this, Thanks
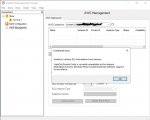
I am trying to configure Scaleout on AWS. I created an AWS connection providing access/secret key. But I got below error when I got to AWS deployment tab. Can you find out why this keeps happening.
Further I want to know is there a way to connect to AWS without providing access/secret keys may be such as using IAM user, roles etc. I am reluctant to use access/secret keys as we have to rotate keys periodically, and lack of security.
Appreciate your inputs on this, Thanks