Hi all, I'm not a Dev, more ops supporting SOSS that I inherited, so jumping into this pretty blind. (Any existing posts/documentation that I missed, feel free to post.)
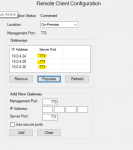
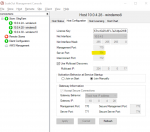
I've got one StateServer supporting 3 environments (remote agents), it was working fine, but yesterday one Test env stopped working. Unfortunately it's being used by a proprietary framework so I don't have much visibility, but main part of error is:
'ScaleoutServiceUnavailableException'><message><